lawd a mercy

I ended up adding traditional AES encryption with public and private keys. So that’s a layer on top of what I already invented.
lawd a mercy

I ended up adding traditional AES encryption with public and private keys. So that’s a layer on top of what I already invented.
do you exchange new keys with each mail?
It only looks up the public key of the recipient. I was going to write code that cached public keys so it didn’t check every time, but I haven’t decided.
The private key stays on the users client locally so it’s not on any server.
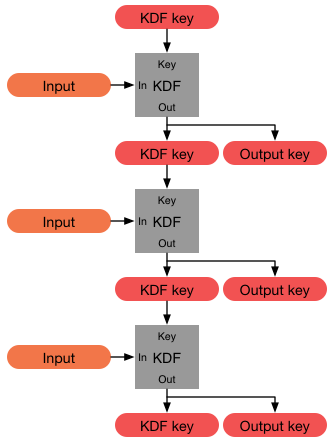

AI Overview
Long-lived keys are dangerous because they increase the risk of a successful security breach, provide attackers with long-term access if compromised, and create vulnerabilities due to potential obsolescence, outdated algorithms, or lack of rotation. If a key is compromised, a long-lived one can give an attacker persistent access, whereas a short-lived key limits the window of opportunity for them.
Risks of long-lived keys
- Persistent access:
A long-lived key that is compromised can give an attacker a persistent access method with the same privileges as the original owner, increasing the potential damage.
- Increased compromise window:
The longer a key is active, the more time an attacker has to steal or crack it, either through brute force, a data breach, or other vulnerabilities.
- Outdated security:
Old keys may use cryptographic algorithms that have since been found to be weak or insecure. Newer, more secure algorithms are developed, and long-lived keys prevent the use of these updates.
- Hardcoding risks:
Keys that are hardcoded into an application's source code are difficult to change and may remain in use long after they should have been rotated or revoked, as seen in issues with hardcoded passwords.
- Lack of rotation:
Without a regular rotation policy, keys are not refreshed and remain static. This increases the risk of exposure, especially if the key was compromised in the past and the organization was unaware of it.
- Personnel changes:
Keys may not be properly revoked when an employee leaves, leaving a potential back door open for unauthorized access. Regular rotation and immediate revocation are crucial for security.
Forward secrecy - Wikipedia
en.wikipedia.org

 So I can just add a function or method that forces key regeneration periodically or on demand.
So I can just add a function or method that forces key regeneration periodically or on demand.So I can just add a function or method that forces key regeneration periodically or on demand.

if you have control on both sides generate a new key pair each time
diffi-hellmann ephemeral keys
but
you can use certificate pinning to .... maybe even in both directions depending on your arch
I promised an update eventually. So instead of my company offering me more money or a new position they decided to FIRE me lmao. Insane experience. Took me 4+ months to find another job, but I start in 2 weeks, make more money than I did previously and it is a 100% remote position in fintech. I can't stress how important it is to have an emergency savings, it was the only way I survived.I have some WILD updates to this entire story that I will post at a later date.
Forgot to mention - the new position they created was basically the position I requested for them to create in the raise letter I submitted. I really don't understand their logic at all here lmao. Instead of just creating the position and promoting me, they fired me -- losing 8+ years of institutional knowledge, which also hamstrung their new hire because I wasn't there to teach him, then ended up creating the new position anyway and bringing in someone new. They were trying to make me wait until next year which is why I started looking elsewhere for work.I promised an update eventually. So instead of my company offering me more money or a new position they decided to FIRE me lmao. Insane experience. Took me 4+ months to find another job, but I start in 2 weeks, make more money than I did previously and it is a 100% remote position in fintech. I can't stress how important it is to have an emergency savings, it was the only way I survived.
Additionally - fukk HR Departments and fukk shytty ass executives. Shortly after they fired me they created a brand new position that was everything I was doing in addition to my position, so I was doing 2 full time jobs for them and they still fukked me. b*stards.
It worked out in the end thankfully. But yeah from your experience i think we all can see you're better off just switching jobs than trying to leverage the situation when you're be overworked and underpaid. These employers see us as expendable and they get upset when we treat them the same. Smh. But hope your new situation is much much better and way less stressfulI promised an update eventually. So instead of my company offering me more money or a new position they decided to FIRE me lmao. Insane experience. Took me 4+ months to find another job, but I start in 2 weeks, make more money than I did previously and it is a 100% remote position in fintech. I can't stress how important it is to have an emergency savings, it was the only way I survived.
Additionally - fukk HR Departments and fukk shytty ass executives. Shortly after they fired me they created a brand new position that was everything I was doing in addition to my position, so I was doing 2 full time jobs for them and they still fukked me. b*stards.
Thanks bro. It was an eye-opening experience. They did me mad dirty. I also couldn't collect unemployment because they fired me for cause. I'm excited for the job, I think it'll be less stressful for sure, and it's a bigger company that offers a bunch of different services, so I'm going to try to eventually worm my way into cybersecurity with them. Fully remote going to be really nice. My previous company was completely against remote work. Lessons were learned here. An absurd way for a 10 year employee that never had a single issue to go out.It worked out in the end thankfully. But yeah from your experience i think we all can see you're better off just switching jobs than trying to leverage the situation when you're be overworked and underpaid. These employers see us as expendable and they get upset when we treat them the same. Smh. But hope your new situation is much much better and way less stressful