Yeah I do
So other than the books did you use any study aids or web sites?
And it seem like it better to take the harder test (ie Comtia Cysa+), first then followed by the CISSP. Is correct?
Yeah I do
Just used the two books mentioned.So other than the books did you use any study aids or web sites?
And it seem like it better to take the harder test (ie Comtia Cysa+), first then followed by the CISSP. Is correct?
I believe a few months ago I said I was targeting the CASP, but I decided to say fukk that and get the CISSP since its rated better in the DoD system
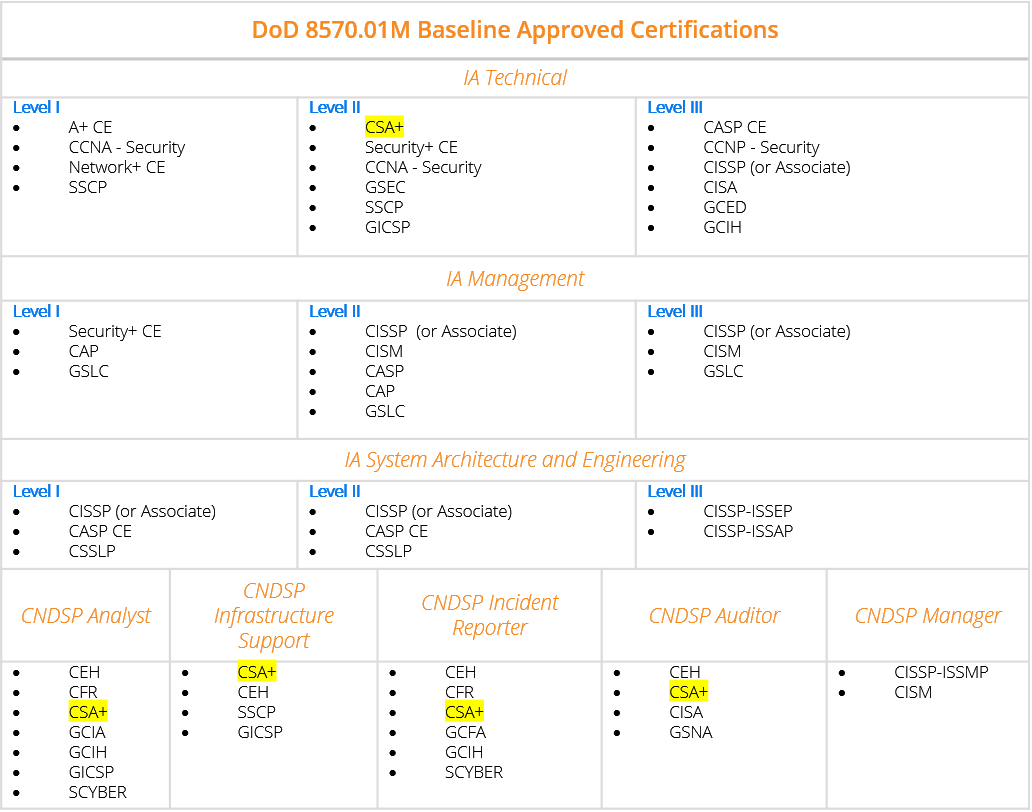
As you see the CISSP has better coverage. Marketability just went up. Again can't stress how good a hustle the government contracting game is to you younger guys wanting to get into the industry and eat. Get your clearances anyway you can, take a bad paying contract to get that Secret or TS and feast.
Now back on topic. Passed the test, must say its one of the easiest tests I've ever taken.
I had 100 questions exactly, I have to say its difficulty is very similar to Sec+ IMHO. You study the Shon Harris book cover to cover, then read the Sybex ISC2 book for refinement of what you just learned and you'll be good.
Any specific questions though and I'm here to help.
You are given a phone to repair and analyze. The customer complaint is that a rogue hacker is illegally monitoring and stalking customer on their phone. The hacker has inserted words, letters, etc while customer is on the phone.
The customer has installed AV, anti rootkit
and anti malware. The customer believe the back is happening at a router/gateway level AND via backdoor app.
The customer needs privacy.
When the phone is on airplane mode and the rogue hacker is still able access to the phone using IMSI catcher and other telecomm hack tools. The hacker has been able to establish rogue web access to phone, but the average phone user cant connect to the web because phone is on airplane mode. All protocols are supposedly turned off.
How would you determine where and how the hacker has illegally established access on the phone?
How would you remove the hackers access?
How would you log and track the hackers on the phone?
How would you prevent the hackers from reaccessing phone and installing backdoor?
Early 30s.You’ve been doing this since ‘03? What’s your age range if you don’t mind?
Try to know by by name was the general purpose of each framework is.Another question, how well do you have to know these different frameworks... shyt is putting me to sleep for real
welcome to the club breh!
We need more CISSPs out there
This is what im most surprised about, because the Sec+ was the easiest cert I ever did.I believe a few months ago I said I was targeting the CASP, but I decided to say fukk that and get the CISSP since its rated better in the DoD system

As you see the CISSP has better coverage. Marketability just went up. Again can't stress how good a hustle the government contracting game is to you younger guys wanting to get into the industry and eat. Get your clearances anyway you can, take a bad paying contract to get that Secret or TS and feast.
Now back on topic. Passed the test, must say its one of the easiest tests I've ever taken.
I had 100 questions exactly, I have to say its difficulty is very similar to Sec+ IMHO. You study the Shon Harris book cover to cover, then read the Sybex ISC2 book for refinement of what you just learned and you'll be good.
Any specific questions though and I'm here to help.
One more on the way brehwelcome to the club breh!
We need more CISSPs out there

This is what im most surprised about, because the Sec+ was the easiest cert I ever did.
Was the CISSP a lot of terms/definitions?
Were there any situational/scenario based questions? What was the most difficult part?
Easier than the A+?This is what im most surprised about, because the Sec+ was the easiest cert I ever did.
Was the CISSP a lot of terms/definitions?
Were there any situational/scenario based questions? What was the most difficult part?
Yep, Motherboard section had me all the way fukked upEasier than the A+?
Easier than the A+?
Did you ever figure out subnetting?Yep, Motherboard section had me all the way fukked up